Author Archive
Stopping e-mail from runaway web sites
by Andrew Macpherson on Apr.10, 2015, under E-Mail hosting
Recently we had a customer whose website was infected by way of one of the infamous plugins that are sometimes bundled into themes, such as TimThumb. The result was their site became one of the foci of a world-wide bot-net which posted tiny abouts of information (greeting and e-mail addresses) to target fairly large SPAM messages out from their site.
This ran overnight at the weekend, so by the time we had tracked it down 25,000 messages had been submitted, all properly validated as coming from the customer’s site
Fortunately 10,000 messages were still in the system outgoing queue, and we were able to purge those, but it was still around 10 days before mail was flowing properly again.
In response to the issue we are “rate limiting” email by number of recipients from each sender. In a time window I’ve run some analysis on the traffic logs, and apart from the mailing lists we host, which would be expected to send to many recipients, and with only 8 exceptions, in the past month no-one sends to more than 10 recipients in an hour. We’ve exempted the known high volume senders from checks, and will be setting a sliding 1 hour window to restrict every other mail account’s submission rates to slightly more than this observed high
This may affect you if you suddenly decide to do a mass mailing. It’s easy to enable your account if you tell us in advance, also don’t forget you can have a hosted mailing list which can individualise each message for its recipient
Perpetual Membership cards
by Andrew Macpherson on Jan.02, 2014, under Technology
Apropos of nothing in particular I was musing on the question of membership/ID cards, and how one cannot readily validate them. This in conjunction with signing in yet another access log led to a thought.
Why not harness the web, and mobile technology?
The method involves using QR codes or similar technology that can be scanned by an app on a smartphone to encode a vCard with the details of the bearer, and containing an https secure link to the validating organisation’s website, where the bearer’s photo, contact details (which should match those encoded) and their status [ member / lapsed | employee / contractor /no longer valid ] can be shown.
It does give rise to the meta-discussion about how far one can trust a website SSL certificate, but it does put some validation tools in the hands of the person presented with the card.
And it gives rapid data-fill for the log.
Be careful about “fixing” problems in your logs
by Andrew Macpherson on Jan.02, 2014, under Operations
One of the things that happens every night on a Linux server is the administrator gets an emailed log file summary from a process known as “Logwatch” with lots of useful information such as a list of sites that have tried to guess passwords, hack your web server and so on. It also tells the current disk usage , warns about things getting out of kilter…
It’s generally a good idea to find what’s causing problems and fix them, but sometimes the answer is to stop reporting the problem.
Amongst the things that are reported when you run a name service are the hosts tHat try to use your server as a recursive resolver (you don’t want to let anyone other than your own customers do this or you might become part of a DDoS attack) and the servers that give malformed responses.
Now as I run a pretty up-to date name server I tend to believe the server when it reports that it’s getting random responses, and had written code to collate the reports to make an exclusion list of servers not to talk to.
Top of the bad response list were ns?.msft.net. These are the name servers which connect you to hotmail.com and outlook.com, and while blocking them gives a noticeable improvement in SPAM volume, ultimately there are people who want to use Hotmail.com despite it’s dreadful record of accounts being hacked
Mail Problems after Email Server upgrade
by Andrew Macpherson on Oct.08, 2013, under Operations
Over the end of last week, and the weekend we had to make an Emergancy upgrade to the mail server. Fortunately for many this was transparent once the DNS had updated, however there are some customers who have email account names which differ from their email address
Mostly those customers can read their email but cannot send new mail
The workround, and I stress this is a workaround not a long term answer, is to add @assp.knots.net to the end of their account name in the sending mail section in the account configuration of your mail program, or the settings app on iOS. Longer term, please contact us at a convenient time for you, and we’ll rename your account to match your mailbox — this will also require setting your password again
Sorry for the nuisance, hope this gets you going
2 signature blocks
by Andrew Macpherson on Feb.01, 2013, under Technology
I smiled when I saw these 2 signatures juxtaposed. The first is my own, on the basis of a government sponsored seminar on copyright and intellectual property, the second is clearly imposed on the sender by their company…
LEGAL CLAIMER:
Any claims made at this point in a message are completely invalid as they are presented after the information they attempt to assert rights over has been disclosed without prior caveatNOTICE AND DISCLAIMER
This e-mail (including any attachments) is intended for the above-named person(s). If you are not the intended recipient, notify the sender immediately, delete this email from your system and do not disclose or use for any purpose.
In the second case, if the sensitive information is solely in the attachments, and the attachment is flagged to be an attachment vs an inline body part, then it might have some slight weight as the contents will not yet have been disclosed.
Really though if you are sending private mail you need end-to-end encryption
How to get your mail blocked
by Andrew Macpherson on Nov.30, 2012, under E-Mail hosting, Operations, SPF the Sender Policy Framework
We spend a lot of time trying to let legitimate mail through, and filtering problem mail into SPAM folders for our customers. Here are a few ways you can ensure you get filtered as SPAM
- Always change the sender of each message, to each recipient, to prevent whitelisting
- Assume that the FROM line will be recognised (it will not, sender is what counts)
- Have an incorrect SPF record for where you are sending from
- Always change the sender of each message, to each recipient, to prevent whitelisting
- Make sure your customers never reply to your mail, use a “noreply” address
- Send mail to customers who report you as SPAMMING them
- Use a 3rd party mailing list service with bought lists
- Send mail containing links to sites that are black-listed
- When doing any of the above, send lots of mail to establish a history of sending dodgy mail
- Always change the sender of each message, to each recipient, to prevent whitelisting
- Slightly less important, have a mismatch between the email sender’s domain, and the system sending it
- Carefully include keywords that trigger automatic traps e.g. “Beneficiary,” “winner.” “prescription,” etc
- Send from a misconfigured system
- Have an invalid Message-id, or none at all.
- Always change the sender of each message, to each recipient, to prevent whitelisting
- Send from a system with a dynamic IP address (home vs business broadband)
- Use words and phrases that differ greatly from the language written by the intended recipient (Bayesean check)
- And remember always change the sender of each message, to each recipient, to prevent whitelisting
After all, it’s all about tracking deliveries, not getting your message through isn’t it?
Poor Joomla Code, again
by Andrew Macpherson on Nov.13, 2012, under Operations
We were asked to install the current version of Joomla (2.5.8) for a customer. Should just be a moment’s work? Not so.
The people who wrote the install code try to do everything with absolute paths. This is fine if you are running on a single-use server. It blows up when one uses cgiwrap to protect the users of a shared server from each other.
To make matters worse, this “Absolute Path” gets calculated in many different places (why?), and I’ve mentioned that I consider Joomla to be totally object obfuscated, and just plain unmanageable before now…
Result: the install script tries to get the server to execute “.js” files, instead of downloading them as part of the page. The visible symptom is that one is stuck on the first install page (lacking the JavaScript to progress)
Solution: install on the sort of simple server the coders anticipated, then copy across, and fix up “live site” in the config file.
What a palaver
WordPress article background picture
by Andrew Macpherson on Jun.14, 2012, under Operations, Technology
Should be easy, right? Slight problem that the result is going to go under the article text, but not the heading, but this should suffice for most purposes.
As always with this sort of question the devil will be in the detail. For instance on our blog here the background is dark, so any background image also has to be dark or risk losing the text.
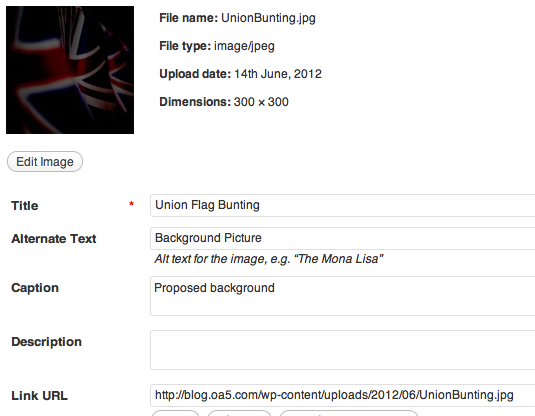
So with this image the problem is the white in the flag, a black layer and a hard light blend soon fixes that. Then upload the background, without inserting it into the post, but pick out where it is stored in the wordpress backend — see the screen shot
The Link URL text is by default the location of the image. Copy this, then cancel out of “insert image”. Now all you have to do is put in a little bit of raw html round your text.
Click the HTML tab at the top of the editor and at the top of your article paste in the url of your background in amongst some magic like this:
<div style="background-image:url(/wp-content/uploads/2012/06/UnionBunting.jpg);
background-size: contain; ">
The background-size: contain element matches the width of the image to your article width. You might also want background-repeat:repeat-y to repeat vertically or background-repeat:none to only put the image in once
At the bottom of your article you need to put in a matching </div> to end the area that will have the image
Social Network Nuisance E-Mail
by Andrew Macpherson on Feb.06, 2012, under E-Mail hosting, Operations
If there’s one thing that’s visible every day, it’s that users (& some administrators/developers) are easily confused.
Take for instance the “Find My Friends” misfeature on most Social Networking sites. None warn the user to go through and check that the invitations they are about to generate are really only going to their friends, and that they should only send mail directly to their friends, not to mailing lists.
I wonder how many suppliers get invitations to connect to customers whom they don’t really know on LinkedIn? How many mailing lists are invited to sign up and befriend FaceBook users? Some sites like Flickr limit their invitations to existing users, others need blocked from every mailing list.
Who is using your email address?
by Andrew Macpherson on Jan.17, 2012, under SPF the Sender Policy Framework
Well you are of course.
Then there are spammers, whom we try to control with SPF records in the DNS to limit where your email can come from to the servers you use.
Then there are misguided websites which try to use your email address to send mail when someone fills in a form claiming to be you. You didn’t send that mail, the website did, so the 4 players in the message should be set appropriately; they are
From — who he message purports to be from — you in this case
Sender — the website administrator
Reply address — again probably you
Error Reports — Probably should go to the website admin
Websites will usually fix this once they understand the problem.
Finally there are people doing stuff for you, for instance payment portal providers, or webservice consolidation sites such as house or employment search services. Most of the above applies, with the added wrinkle of you as the named responsable (EU French term for the person accountable) for the service.
The portal will correctly show you as the From address, but should not be using your email as the sending address that’s just simply wrong, if you do agree to it then the portal should provide a portal SPF record that can be included by your own SPF record, how otherwise are you supposed to maintain your email security with random contractors thinking they can send as though they are you vs someone providing a service to you?
One does not use another company’s headed notepaper after all. That’s fraud. Why then should you use another company’s email address, without making the ‘on behalf of‘ relationship clear?